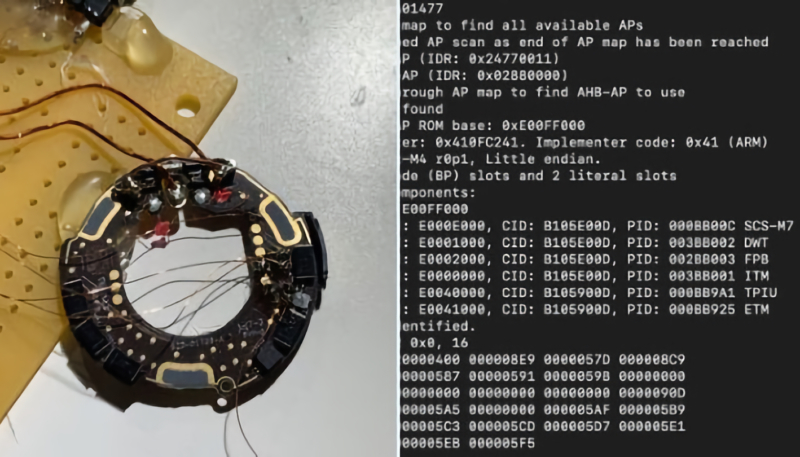
A security researcher has hacked Apple’s new AirTag and has modified its software. German security researcher “Stack Smashing” announced on Twitter that they were able to “break into the microcontroller” of the AirTag.
The tweet was posted on Saturday and first reported by The 8-Bit, the tweet thread includes a few details about the prodding of the device.
Built a quick demo: AirTag with modified NFC URL 😎
(Cables only used for power) pic.twitter.com/DrMIK49Tu0
— stacksmashing (@ghidraninja) May 8, 2021
This is important as Apple is well-known for building high levels of security into its products. This makes the new accessory an attractive target for security researchers.
After destroying multiple AirTags, the researcher dumped the device’s firmware, discovering that the microcontroller could be reflashed. The researcher proved that programming of the microcontroller to change how the device functions is possible.
The researcher offered a demonstration that showed how an AirTag had its NFC URL modified to display a custom URL in place of the “found.apple.com” link when scanned by an iPhone.
It should be noted that the demonstration video showed the modified AirTag attached to cables, which are claimed to be used only for powering the device.
While this “hack” shows that similar techniques could be used by the bad actors of the world, it isn’t quite clear how far this could currently be pushed.