Several Apple customers have reported being targeted in elaborate phishing attacks that involve what appears to be a bug in Apple’s password reset feature, according to a report from KrebsOnSecurity.
The users have been targeted in an attack that bombards them with an endless stream of notifications or multi-factor authentication (MFA) messages in an attempt to get them to approve an Apple ID password change.
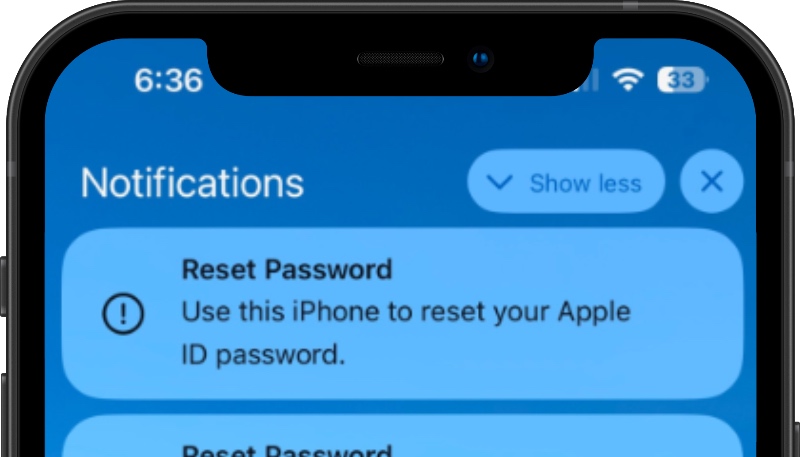
In this scenario, a target’s Apple devices are forced to display dozens of system-level prompts that prevent the devices from being used until the recipient responds “Allow” or “Don’t Allow” to each prompt. Assuming the user manages not to fat-finger the wrong button on the umpteenth password reset request, the scammers will then call the victim while spoofing Apple support in the caller ID, saying the user’s account is under attack and that Apple support needs to “verify” a one-time code.
The password requests target the Apple ID, meaning they show up on all of a user’s devices. The linked Apple devices are all useless until the popups are dismissed on each device one by one.
If attackers are unable to trick the user into clicking “Allow” on the password change notification, targets then get phone calls that appear to be coming from Apple. On the call, someone posing as Apple Support says they know the victim is under attack and tries to learn the one-time password the user is sent when attempting a password change.
In some of the attacks, attackers are using information leaked by a people search website, which includes name, current address, past address, and phone number, which is more than enough info for an attack like this. The attack seems to rely on the bad actor having access to the email address and phone number associated with an Apple ID.
In one case, a user became suspicious when the attacker had his name wrong, and the attacker asked for the one-time code that Apple sends with an explicit message saying Apple does not ask for those codes.
KrebsOnSecurity investigated the issue and found that the attackers appear to be launching the attack by using Apple’s page for a forgotten Apple ID password. The page requires a user to enter their Apple ID email or phone number. The form has a CAPTCHA to prevent robo-usage. When the user enters their email address, the page displays the last two digits of the phone number on the account. Filling in the missing digits in the phone number sends a system alert.
The attackers are somehow abusing the forgotten email recovery system via a bug that is being exploited.
Apple device owners targeted by this kind of attack are advised to carefully tap “Don’t Allow” on all requests and should remember that Apple does not call you on the phone requesting one-time password reset codes.