A now-fixed exploit in the macOS version of Microsoft Office could have allowed bad actors to hack a Mac user’s machine just by getting them to open an infected document.
The exploit was developed by Jamf security engineer and ex-NSA hacker Patrick Wardle, who specializes in hacking Macs. Wardle revealed the attack method at the Black Hat 2020 security conference Wednesday.
As revealed on Wardle’s blog, the exploit takes advantage of Microsoft Office’s macros feature.
In the world of Windows, macro-based Office attacks are well understood (and frankly are rather old news). However on macOS though such attacks are growing in popularity and are quite en vogue, they have received far less attention from the research and security community.
Macros, which are basically small programs embedded in files, were only one part of the exploit. Wardle said he had to string together several vulnerabilities to get the exploit to work.
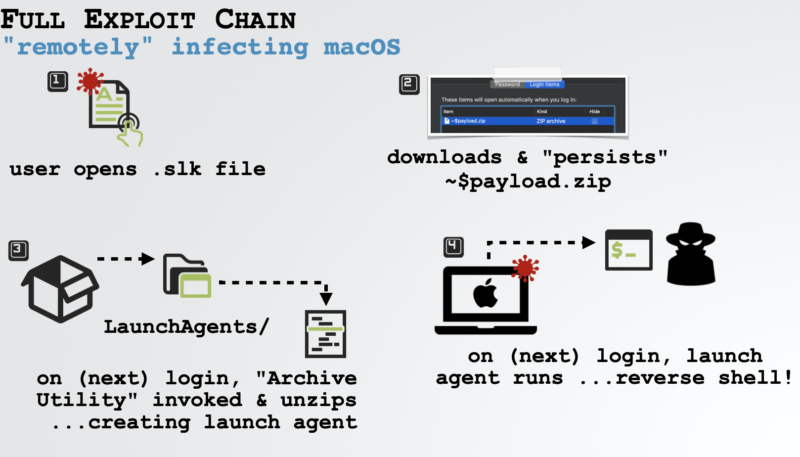
As noted by AppleInsider, Wardle was able to get Office to run macros without alerting the user by creating a file with an old .slk format. Adding a “$” character to the start of the filename allowed Wardle to escape the protective macOS sandbox. Wardle then zipped the file into a .zip format — which macOS doesn’t check against its notarization requirements.
By using this method, Wardle was able to create an exploit that only required users to double-click a Word document. Wardle admits that a user still needs to authenticate some of the actions by logging in. But if the user does authenticate it, malicious files and backdoors could be installed by an attacker.
The vulnerabilities that Wardle leveraged were patched in the latest version of Office on Mac and macOS 10.15.3.
Wardle told Motherboard he alerted both Microsoft and Apple of his findings but says Apple never responded.