A bug in the macOS Quick Look functionality can expose sensitive user information like photo thumbnails or the text in documents, even that which is stored on encrypted drives.

Details on the Quick Look flaw were shared earlier this month by security researcher Wojciech Regula and over the weekend on security researcher Patrick Wardle’s blog (via The Hacker News).
Quick Look allows macOS users to quickly view a zoomed-in view of a photo or document in Finder by pressing the space bar when a document is selected.
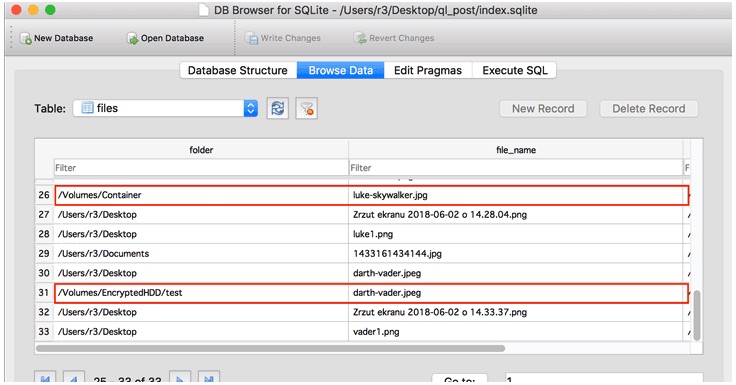
To provide this convenience, the Quick Look feature generates thumbnails for each file/folder, providing a convenient way to view files before they open them. The thumbnails are stored in an unencrypted database. The thumbnails can be viewed by any individual with the proper know-how, and there is not automatic cache clearing functionality included in macOS to delete them.
Regula explains:
It means that all photos that you have previewed using space (or Quicklook cached them independently) are stored in that directory as a miniature and its path. They stay there even if you delete these files or if you have previewed them in encrypted HDD or TrueCrypt/VeraCrypt container.
Though not widely known by Mac users, the issue has reportedly existed in Mac OS X/macOS for at least eight years, and alarms have been raised about it in the past, but Apple has yet to offer a fix for the issue.
“The fact that behavior is still present in the latest version of macOS, and (though potentially having serious privacy implications), is not widely known by Mac users, warrants additional discussion,” says Wardle.
This information is valuable to both law enforcement and the bad guys who would have access to a historic record of the user’s Mac hard drive, and any USB storage device that’s been attached to the Mac.
For a forensics investigation or surveillance implant, this information could prove invaluable. Imagine having a historic record of the USB devices, files on the devices, and even thumbnails of the files…all stored persistently in an unencrypted database, long after the USB devices have been removed (and perhaps destroyed). For users, the question is: “Do you really want your Mac recording the file paths and ‘previews’ thumbnails of the files on any/all USB sticks that you’ve ever inserted into your Mac?” Me thinks not…
If a Mac’s main drive is encrypted, then the Quick Look cache is also encrypted. So the data in the cache might be considered “safe” when the Mac is turned off. However, the information is available when the computer is turned on and a user is logged in.
Wardle recommend users who might be concerned about the contents of their Quick Look cache clear the cache when a container is unmounted. Instructions for the process are available on Wardle’s website.