Mac security researchers have discovered two separate cases of new malware aimed at Mac users and their machines. 9to5Mac notes both of the exploits rely on unsophisticated Mac users clicking something they shouldn’t.
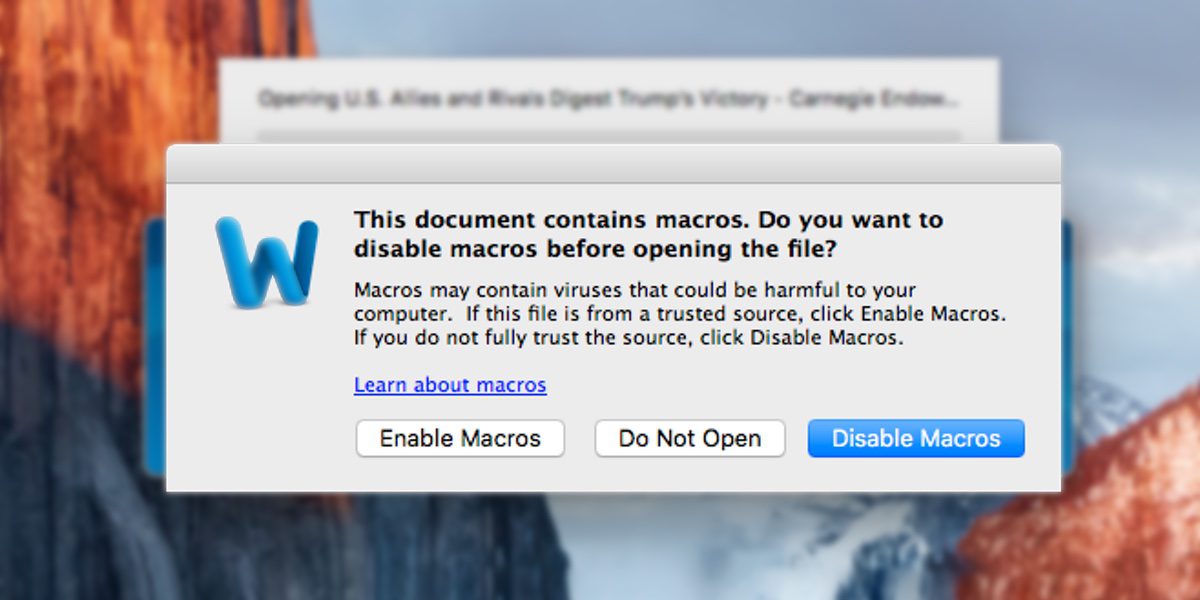
Mac Attack # 1: Word Macro
The first malware exploit uses an old Windows technique, executing code inside Microsoft Word documents using macros. The exploit is believed to be the first of its type aimed at the Mac.
The exploit works by having unsuspecting users open a specially-crafted Word document that includes macros that run when the file is opened. Macros were a prevalent attack vector in the Windows world many years ago and it now seems at least one organization is attempting to use the primitive methods on Mac users.
Infection is easily avoided, as the document, when opened in Word, (not Pages), will prompt the user for permission to execute the malicious code. Users need only to click “Disable Macros” to prevent the code from running. Users who grant permission are allowing the macros to download malicious code and execute it.
The bad code could perform key logging, monitor your webcam, grab your browser history, and more. Researchers found the exploit in a file called ‘U.S. Allies and Rivals Digest Trump’s Victory.’ (Insert political commentary and humor here.)
The attack is truly primitive, and hopefully won’t fool many folks, as even the Office popup itself recommends users click the “Diable Macro” button, and offers up warnings about the consequences.
Mac Attack #2: Fake Flash Player Update
The second instance of malware discovered this week also relies on an “oldie but a goodie” attack, presenting itself as an Adobe Flash Player update. The “update” actually grabs a copy of the user’s Keychain, phishes for usernames and passwords, and harvests other personal information wherever it may be available. The data is then sent back to a remote location.
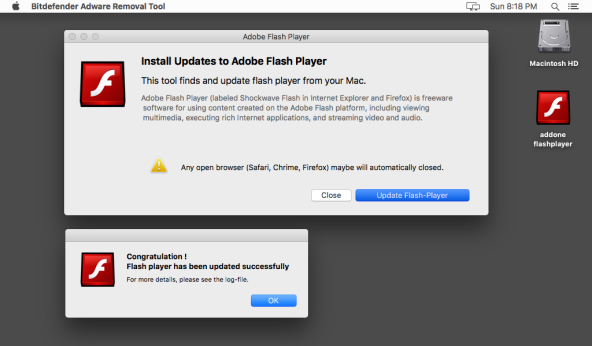
The attack is also easily avoided as it relies on the user clicking on a link to update their Mac’s Flash Player plugin from a website they have visited, (or have been taken to via a popup), and then running the downloaded file. Users can easily avoid an attack of this type by only updating apps and plugins via their Mac’s Software Update mechanism, or by visiting the plugin site directly. (Or users can simply uninstall Flash completely, removing the temptation, and also closing a huge, commonly used, security hole.)
As always in cases like this, we’d like to remind our readers that while Mac viruses and exploits are nowhere near as common as those affecting Windows machines, they are still out there, waiting to attack unknowing Mac users and their machines. Always practice smart computing, and think before you click.


